Month: June 2013
-

Data Mining the Electorate
The New York Times Magazine had a cover piece on the Obama data mining team that used modern data-mining techniques to more efficiently target the undecided voters that they needed to bring across the fence to win the election. Check out the last line (emphasis mine) on their clever use of Facebook photo tags as…
-

Unintended use for Microsoft Kinect
I ran across this interesting use for Microsoft Kinect by an MIT Researcher who was featured in the latest issue of The Red Bulletin, a print sports lifestyle magazine that magically shows up on my doorstep every month. The article (I cannot link to it because I cannot find it online), which profiles urban planner…
-
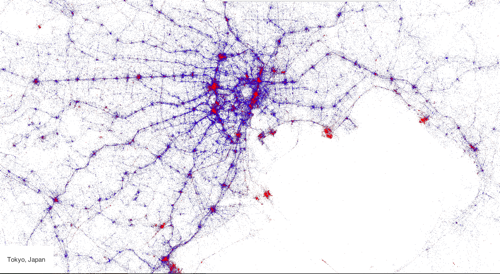
Digital Contrails
What do you do when you have access to the twitter firehose and a top notch geo-visualization artist? Make beautiful maps of course! Gnip and Eric Fischer got together with MapBox and plotted millions of tweets by location, language, and device to come up with some fantastic interactive maps. The map above is Tokyo…
-
Patently Ridiculous
I had a listen to the second part to This American Life’s excellent two part series on patent trolls (the first part is here) and how the use of weaponized software patents is squashing innovation. The podcast outlined the plight of entrepreneurs too afraid to start business for fears of being sued out of existence…
-
Autonomous Robotic Weapons
Daniel Suarez is one of my favorite SciFi writers because he takes the technology trends happening today and draws a line into the future to warn us of what dystopian nightmare awaits if we take the humanity out of technology. I have recommended his book, Daemon to many people as a must read if you’re…
-

How Design Can Defeat Technology
The Offline Glass from Mauricio Perussi on Vimeo. Maybe not the most practical if you’re worried about condensation getting all over your phone but it certainly does make a statement. The Offline Glass needs your phone to keep it from tipping over, thus forcing you to put your device down and engage with those around…
-
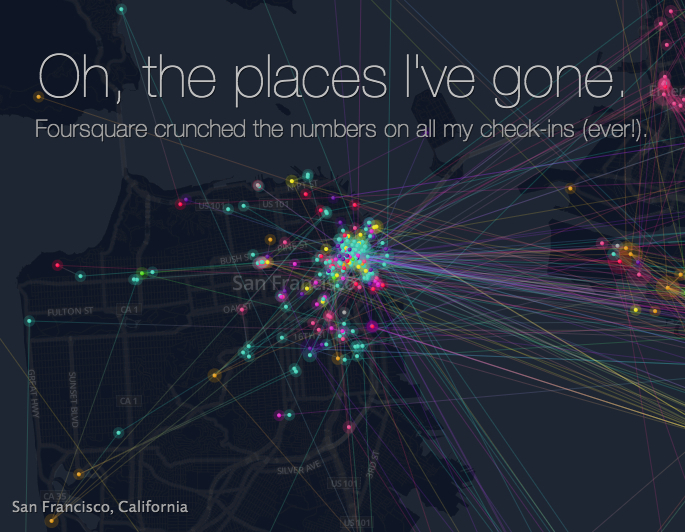
Visualizations – Foursquare and Twitter
Foursquare and Twitter both released experiments that let you look at a visualization of your activity on that service over time. One is art that happens to convey information and tell a story of your travels thru time and space. The other is a functional dashboard that is designed to give you and idea of…
-
Google Japan – Design
My good friends Astrid Klein and Mark Dytham were contracted to design the Google offices in Japan. Google asked them to integrate design motifs from the host country and, as is their style, they re-purposed everyday objects such as Japanese Sentō murals, giant car wash brushes, and soba stand noren to great, playful effect. More…
-

NSA Everywhere
They set about remotely penetrating communications systems and networks, stealing passwords and data by the terabyte. Teams of “vulnerability analysts” searched hundreds of computers and servers for security holes, according to a former senior CIA official involved in the Stuxnet program. Armed with that intelligence, so-called network exploitation specialists then developed software implants known as…