Tag: privacy
-
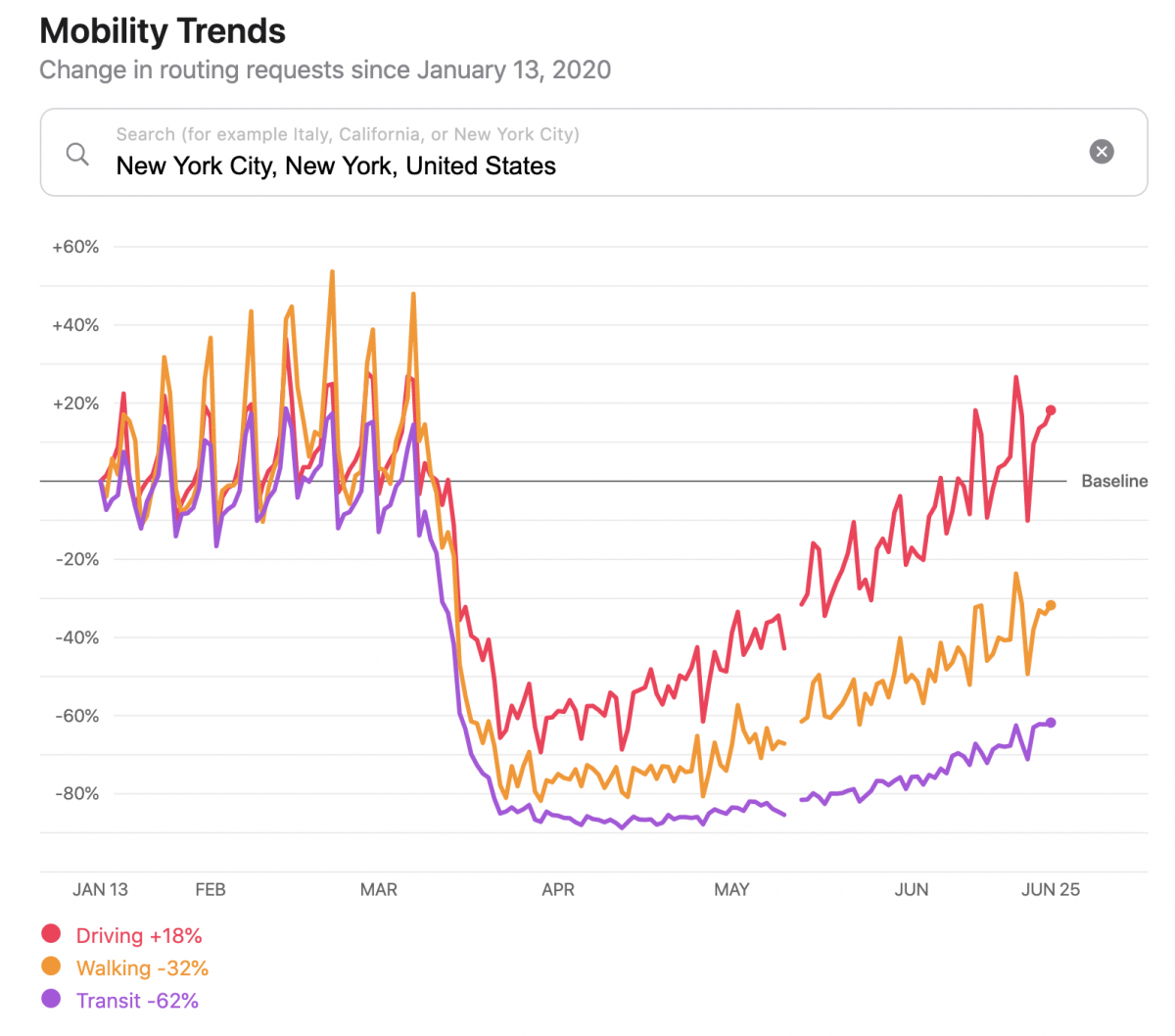
Apple Publishes Mobility Data
Apple published an interesting visualization of data they have on the number of times Apple Maps users looked up directions and how the frequency has changed during the pandemic. The Mobility Trends Report is not only a great way to show the value of Apple’s aggregate data but also an opportunity for the company to…
-

Social Shaming in Cape Town
Cape Town South Africa is facing the third year of an unprecedented drought. Water levels have dropped to such levels that city officials predict the city wells will run dry sometime in 2019. There is, of course, a ban on filling your swimming pool or washing your car and individual consumption is limited to 50…
-
Connected Address Book
Joseph Smarr’s blog post, Turns out we still need Plaxo (or something like it) had me digging through my archives for some screenshots taken from an old prototype I worked on a few years back. The concept was simple and combined the double opt-in privacy features you get from Facebook with the simplicity of a…
-
Privacy Wall
I wrote the following post on Friday and was going to mull it over for a bit but then this article came out in today’s Washington Post that made the issues raised here all the more timely. An interesting topic was brought up that was glossed over in coverage of Friday’s Search SIG. John Battelle…